OpenVPN is an open-source solution for implementing Virtual Private Network to create point-to-point or site-to-site connections. In this article, we will learn how to configure OpenVPN in the pfSense firewall. PfSense is an open-source firewall/router based on FreeBSD currently supported by Netgate.
- Also Read: Install OpenLiteSpeed Web Server on Ubuntu
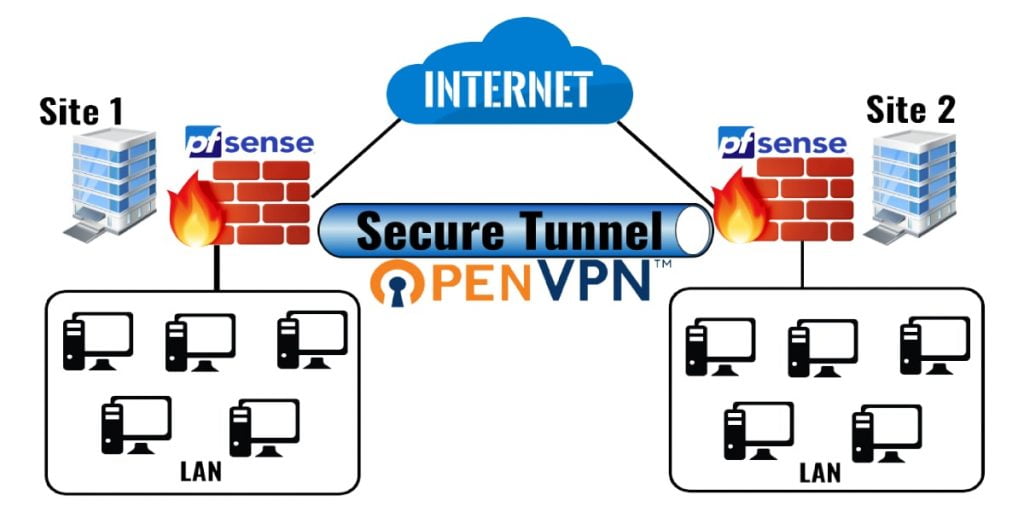
Table of Contents
Prerequisite:
We have required at least two pfSense firewalls in the working state to configure OpenVPN in the pfSense firewall. Follow this article to install and initialize the pfSense firewall if you do not have it yet.
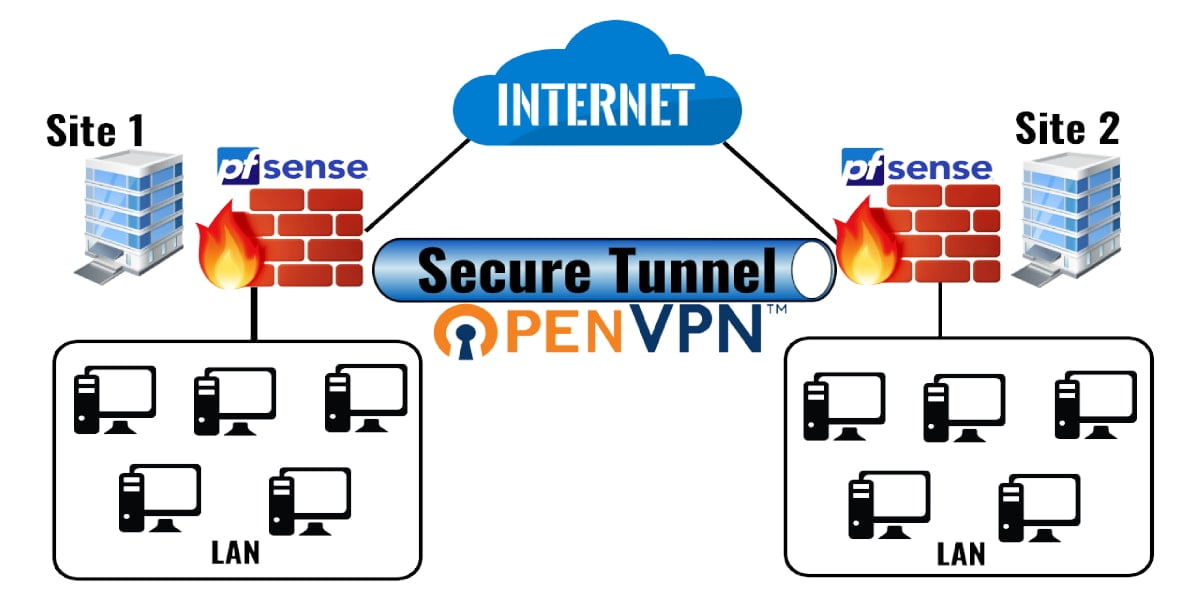
In our current scenario, we have two different sites at different geological locations. Site A and Site B both having pfSense instances as their main Router and Firewall. Here we want to configure a secure OpenVPN tunnel so that the clients from Site A can communicate with the clients of Site B directly.
OpenVPN can configure in two ways, by using a shared key or using SSL/TLS. In this article, we use the Shared Key method to configure it.
Understanding the Scenario
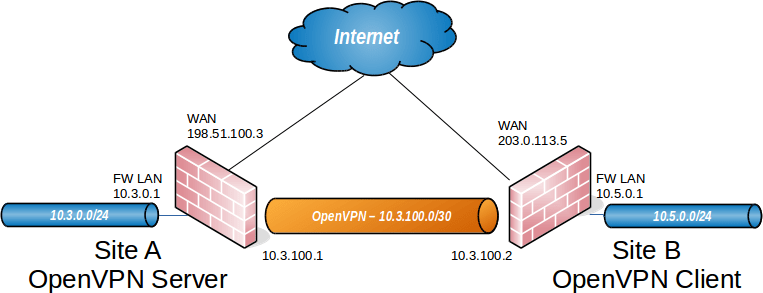
In a site-to-site OpenVPN connection, one firewall will be work as the server and the other will be work as the client. Usually, we configure the main location as a server and the remote locations as clients, while it will work the same if we do the opposite. A dedicated subnet used for the OpenVPN tunnel between networks apart from existing subnets at both ends, similarly as remote access OpenVPN configuration. The above OpenVPN Site-to-Site Scenario use in this example configuration.
In this example, 10.3.100.0/30 is our Tunnel Network. Because an IP address of this subnet is used by each end of the OpenVPN tunnel. As shown in the above diagram. Finally, the next sections describe how to configure OpenVPN Server and Client in the pfSense firewall.
Configuring OpenVPN Server in pfSense at Site A
- After login goto VPN > OpenVPN > Server tab
- Click on Add button to create a new VPN server
- Fill the below fields with described options and leave other fields as defaults.
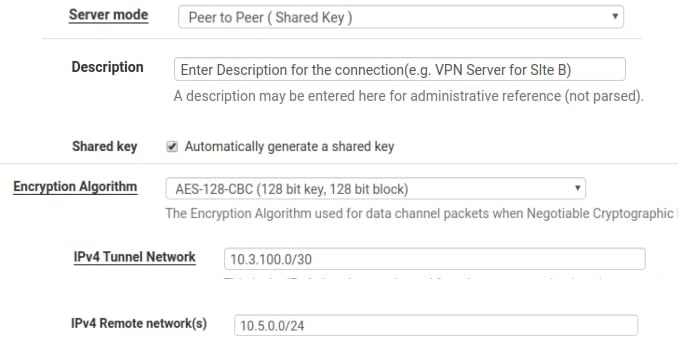
- Server Mode – Select Peer to Peer (Shared Key) option from the dropdown menu
- Description – Enter Description for the connection(e.g. VPN Server for Site B)
- Shared key – Check on Automatically generate a shared key option
- Encryption Algorithm – Select AES-128-CBC (128-bit key, 128-bit block) option from the dropdown menu
- Tunnel Network – Enter 10.3.100.0/30 as our tunnel network
- Remote network – Enter the LAN address of Site B, 10.5.0.0/24
- Now Click on Save button
- After that, click on to edit the server that in the last step
- Look for the Shared Key option
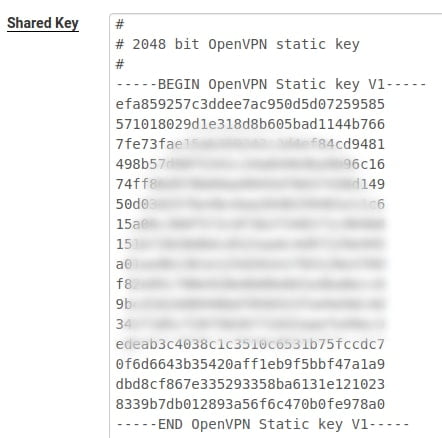
- Select all text from the Shared Key textbox
- Copy the text and save it to a file
After that, add a firewall rule on the WAN interface to allow access to the OpenVPN server.
- Now goto Firewall > Rules, WAN tab
- After that, click on the Add button to create a new rule at the top of all rules
- Select UDP from the protocol dropdown option
- In the Source address option. If the Site B WAN interface has a dynamic IP address, then leave it to ANY. Otherwise, follow the below step for adding the rule to allow only from the WAN IP address of the client:
- Select Single Host or Alias from the Source dropdown menu
- Enter the WAN address of the client in the Source Address field ( in this example it is 203.0.113.5)
- Select the WAN Address option from the Destination dropdown menu
- Enter 1194 in both the Destination port fields
- Enter a Description, such as Rule for VPN Site B
- Click on Save to save the firewall rule.
- Now click on Apply Changes to activate the rule. The rule will look like the image below.
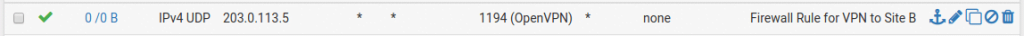
Add a firewall rule to OpenVPN interface at Site A
We have to add one more firewall rule to allowing traffic from the client-side LAN network to the Server-side LAN network through the VPN tunnel. For this, we add an ‘Allow All’ rule in the OpenVPN tab.
- Goto Firewall > Rules, OpenVPN tab
- Now click Add to create a new rule above all existing rules
- After that, select Any from the Protocol dropdown menu
- Now Enter a Description like ‘Allow all from VPN Client‘
- After that, click on Save
- Click Apply Changes to activate the rule and applying changes. The rule will look like the below image.

Here our server configuration is finished. Now we have our working OpenVPN Server at Site A. So let’s move to the client-side configuration.
Configuring OpenVPN Client in pfSense at Site B
- Goto VPN > OpenVPN, Client tab in the client-side pfSense
- Click on Add button to create a new OpenVPN client
- Now fill the below fields as shown, and leave everything else as default
- Server Mode – Select Peer to Peer (Shared Key) option from the dropdown menu
- Server host or address – Enter the public IP address or hostname of the OpenVPN server here (e.g.
198.51.100.3) - Description – Enter Description for the connection(e.g. VPN Server for Site A)
- Shared key – Uncheck Automatically generate a shared key option, then paste the shared key which we saved in a file during server configuration.
- Tunnel Network – Enter 10.3.100.0/30 as our tunnel network (Tunnel Network must be same on both side)
- Remote network – Enter the LAN address of Site B, 10.3.0.0/24
- Now click on Save
Add a firewall rule to OpenVPN interface at Site B
Again, We have to add one more firewall rule to allowing traffic from the Server-side LAN network to the client-side LAN network through the VPN tunnel. For this, we add an ‘Allow All’ rule in the OpenVPN tab.
- Goto Firewall > Rules, OpenVPN tab
- Now click Add to create a new rule above all existing rules
- After that, select Any from the Protocol dropdown menu
- Now Enter a Description like ‘Allow all from VPN Tunnel‘
- After that, click on Save
- Click Apply Changes to activate the rule and applying changes.
As a result, here we completed the client-side configuration. Nothing more is required for OpenVPN configuration. You can just test the connection now.
Summary:
So in this article, we had learned OpenVPN configuration in the pfSense firewall. You can ask for any queries in the comment section. You can suggest to me if I missed something in the article.
I will follow this instruction soon. I will be setting up similar scenario. Thank you very much for this detailed instructions.